Press the Essential Form to Start Your Trial!
Independent Healthcare Sales Representative
Income Potential $150,000 per year.
We are seeking professional Sales Representatives to fill roles across the entire United States. We look for Independent Commission Only Sales Reps with business to business Healthcare sales experience.
Job Location: All Territories across the United States.
The Sales Representative will be responsible for cold calling, selling, and creating new relationships with physicians within the assigned territory while maintaining existing relationships.
Requirements:
- Candidates must have strong qualification, prospecting, closing, objection handling, presentation and account selling skills.
- Possess fortitude to handle rejection while being self motivated.
- Ability to quickly build strong relationships and customer loyalty.
- Manage administrative responsibilities.
Qualifications:
- College degree preferred but will consider strong sales background in lieu of.
- 4 year B2B or Medical sales experience preferred but, will consider recent college graduate with some sales experience.
- Consistent track record of quantifiable sales accomplishments.
- Ability to interface with client counterparts.
- Must have computer, high speed internet access to submit call reports and possess computer Skills: (i.e. Outlook, Word, Excel).
Please send resumes to Info AT HANA.EXPERT.
Cyber Security Consultant - Information Security Subject Matter Experts
Responsibilities:
- Build and entrench credibility with clients on matters of cyber security.
- Assist clients in interpreting risk assessment results and validation of plans to address specific cyber risk issues.
- Provide expertise with clients and account managers on risk mitigation.
- Collaborate with the cyber team in the development, implementation and ongoing improvement of products and services, while gaining understanding of the company's business.
- Support the assessment tool and business process.
- Assist with training and development of cyber security program.
- Responsible for staying abreast of industry standards and trends.
- Travel required.
Qualifications:
- Minimum of 8 years of experience working in information technology with at least 5 years specifically working in the information/cyber security field.
- Experience with one or more of the following; security risk assessments, development of security standards, cyber security risk consulting and incident management.
- Strong knowledge of operating systems and networks.
- Strong knowledge of computer vulnerabilities, hacker methodologies and other threats.
- Strong knowledge of widely recognized cybersecurity risk frameworks (ie; NIST, ISO etc) and how to apply them within enterprise organizations.
- Experience working with enterprise-level information security programs, including governance, risk assessment, policy/standards, technical controls, oversight and assurance, risk treatment, and security education/awareness.
- Ability to leverage various trusted sources of information (articles, webinars, internet, etc) to gain accurate and updated knowledge on cybersecurity and recommend appropriate solutions.
- Excellent verbal, written and presentation skills. Exemplary consultative skills a must.
- Strong interpersonal and organizational skills; attention to detail.
- Strong collaboration and decision making skills.
Education:
- Bachelor degree in Information Security or a related discipline.
- CISSP designation is preferred; other relevant industry certifications may be considered.
Please send resumes to Info AT HANA.EXPERT.
Big Data Analytics Subject Matter Experts Consultant
Qualifications:
- Healthcare Industry Experience.
- 5+ years of hands-on technical experience mining and analyzing transactional electronic data with a strong working knowledge of relational databases, including advanced experience with query building.
- Exposure to advanced analytics concepts such as predictive analytics or machine learning.
- Strong command of data warehousing, data architecture, data quality processes, data warehousing design and implementation, table structure, fact and dimension tables, logical and physical database design, data modeling, reporting process metadata, and ETL processes.
- Experience designing and implementing reporting and visualization for unstructured and structured data sets.
- Experience designing and developing data cleansing routines utilizing typical data quality functions involving standardization, transformation, rationalization, linking, and matching.
- Expertise in building data visualizations with a strong understanding of the appropriate chart types to use to highlight patterns in the data.
- Experience in data modeling, analysis, design, testing, development and implementation.
- Experience publishing dashboards and data sources as well as managing access, user security, and refreshing of Tableau, QlikView, Business Objects Data files / extracts.
- Demonstrated ability to communicate effectively to management.
- Demonstrated ability to balance multiple projects with the strong ability to properly delegate and meet deadlines.
- Professional demeanor and strong communication skills, both written and oral.
- Commitment to personal and professional growth, including the development of peers and junior staff.
- Outstanding integrity, initiative, creativity, and passion.
- Travel required.
Education: Bachelor's degree (BS or BA).
Preferred:
- Experience with C# (.Net) or other programming languages
- Previous Big 4 or major consulting experience.
Please send resumes to Info AT HANA.EXPERT.
HANA.EXPERT and F-Secure - Security Rapid Detection Service - Video
HANA.EXPERT's Rapid Detection Service helps prepare your organization for advanced cyber attacks, before and after they happen. Our fully managed service is designed to detect the most skilled of attackers, whether they're using malware or non-malware tactics, techniques, and procedures. It enables you to respond to threats promptly, with actionable guidance from our experts. Attackers will first gain access to your IT infrastructure. This typically happens either by exploiting a known vulnerability in one of your servers, or by using a combination of spear-phishing emails and a web or document exploit targeting, for example, one of your customer-facing teams.
After gaining the initial foothold in your IT infrastructure, the attackers will try to access the data or gain the control they are after. Typically, they accomplish this by using existing IT administrator tools included in Windows, Mac and Linux operating systems such as PowerShell, Windows Remote Management and Service Commands.
In a 1300-node customer installation, our sensors collected around 2 billion events over a period of one month. Raw data analysis in our backend systems filtered that number down to 900,000 events. Our detection mechanisms and data analytics then narrowed that number to 25. Finally, those 25 anomalies were analyzed and handled by experts, and 15 were confirmed by the customer to be actual threats. In each of these 25 cases, our Rapid Detection Center alerted the client within 30 minutes from the moment the anomalies were flagged.

For more information, please contact:
Sales at 302 715-0062 or This email address is being protected from spambots. You need JavaScript enabled to view it.
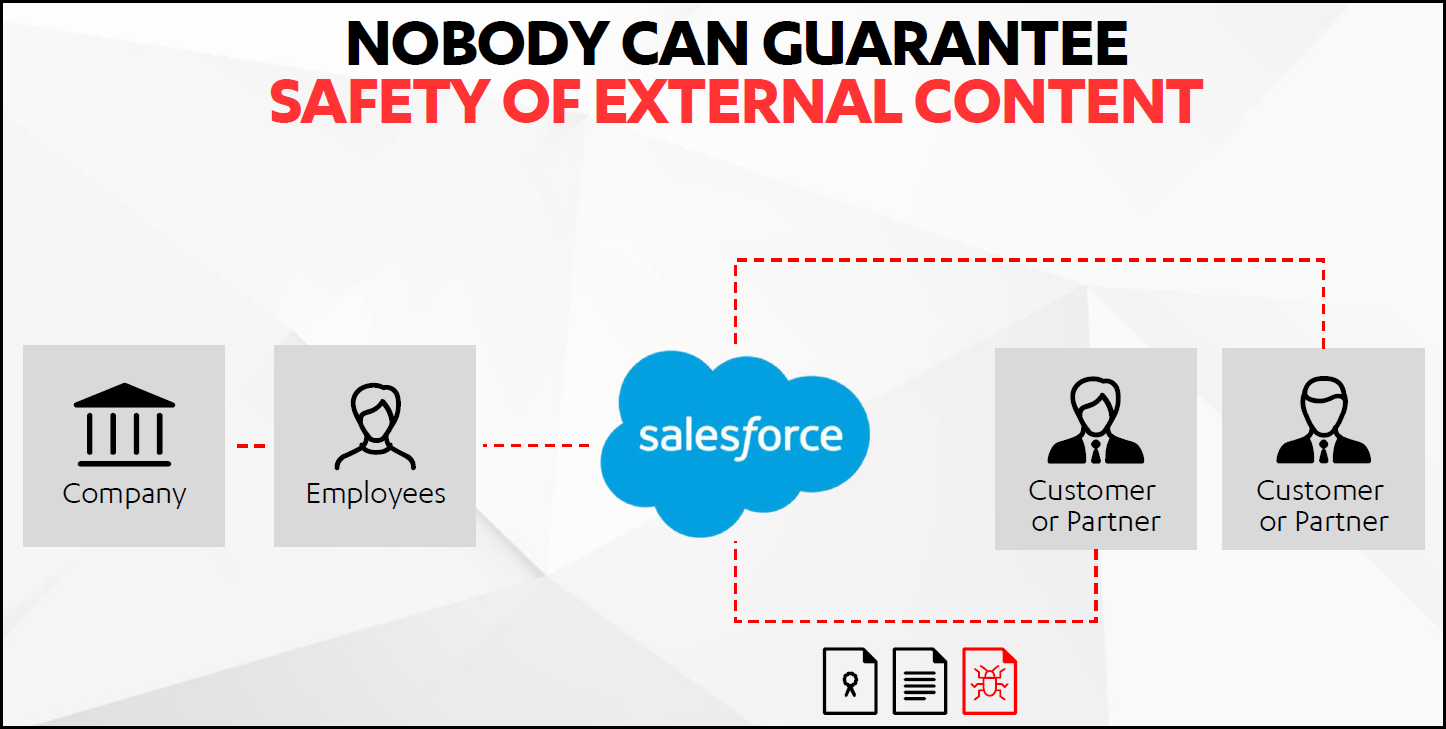
HANA.EXPERT Healthcare Cloud Protection for Salesforce.com is the only security solution on the market designed to prevent attacks via files and URLs uploaded to Salesforce.com.
Cloud ecosystems operate on a shared security responsibility model. Salesforce.com does a great job of covering various aspects of system and application level security. However, it is Salesforce.com subscribers' responsibility to secure files and links uploaded to Salesforce.com platforms by their customers and employees.
It's an essential component of your overall security strategy, and thanks to its Cloud-to-Cloud architecture, requires no middleware. As progressively more organizations outsource more of their IT infrastructure to the cloud, the duties of security personnel have changed, but not vanished — which is confirmed by the proliferation of ransomware and malware threats to cloud-based services.
However, customer security responsibilities differ across the spectrum of cloud-based service models. This variation in liabilities and duties between clients and providers requires that security professionals have a strong understanding of the Shared Responsibility Model.
This means understanding the general trends in Shared Responsibility Models across types of services as well as the individual details of shared responsibilities within the context of each specific service. In general, as the extent of outsourcing to the cloud increases, the security responsibilities of providers grow. Nevertheless, customers of cloud-service providers are always responsible for the content and data on the cloud as well as the user endpoints that access the cloud. For this reason, it is important to consider cloud-based security solutions that complement the security features offered by cloud service providers, with preference given to security solutions that work natively within the cloud.
There are many factors to be aware of when reviewing cloud-based services, but there are at least three key directives that should always be followed: (1) include the cloud in your business and security strategy, (2) understand your responsibility, and (3) choose your vendor carefully. Despite the changing landscape of threats and vulnerabilities, security personnel must not forget the basics of cyber security — the latest cloud innovations will never change sound fundamentals.
CISOs and security leaders must understand the scope of their responsibilities for security in the cloud. Provider-supplied security differs among infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) models.
- Regardless of the model, data security as well as identity and access management (IAM) remain customer responsibilities.
- The cloud reduces the scope of required traditional security work, but cannot eliminate it. Moving processes to the cloud does not automatically make them "more secure".
- Establish a security control plan using third-party tools to achieve better visibility, data security, threat protection, and compliance — preference should be given to third-party tools that are integrated directly into the cloud platform without middleware.
- Fully leverage provider-supplied security measures, and avoid solutions that interfere with, bypass, or reduce provider-supplied security measures.
- The Shared Responsibility Model of course applies to compliance just as it does to security, so make sure you understand the compliance requirements of all aspects.
- Do not settle for cloud partners or third-party solution providers that cannot demonstrate proven security levels through tests conducted by independent firms (e.g., AV-Test and AV-Comparatives).
- Most traditional security best practices still apply to public cloud systems, such as defense in depth and the necessities of next-gen anti-malware, security controls, logging, reporting, and alerts.
Shared Responsibility Model
- The customer is both accountable and responsible for all aspects of securing and operating solutions when they are deployed on-premises.
- With IaaS deployments, elements such as buildings, servers, networking hardware, and the hypervisor, should be managed by the platform vendor. The customer is responsible or has a shared responsibility for securing and managing the operating system, network configuration, applications, identity, clients, and data.
- PaaS solutions build on IaaS deployments, and the provider is therefore additionally responsible for managing and securing the network controls. The customer is still responsible or has a shared responsibility for securing and managing applications, identity, clients, and data.
- With SaaS systems, a vendor provides the application and abstracts customers from the underlying components. Nonetheless, the customer continues to be accountable, must ensure that data is secure and free of malware, and shares the responsibility of managing their users and endpoint devices.
Modern ways of working have demanded collaboration and data sharing approaches that heavily utilize cloud-based services. Unfortunately, as individuals share data through cloud applications, they risk the spread of malware designed to infect these systems. As noted previously, the systems of 11% of organizations have explicitly sanctioned cloud apps infected with malware.
As many organizations provide direct access for cloud applications through their firewalls and other network security functions, protection against malware, ransomware, and malicious links is often left solely to endpoints. This makes systems more vulnerable to attacks and boosts the likelihood of successful attacks — and this exposure becomes worse as the number of complementary security layers decreases.
Furthermore, in instances like the Cerberus attack targeting an Office 365 vulnerability, the chance of spreading the malware to other parts of the organization increases significantly — notably in use cases such as intranets, customer and partner communities, or any other cloud platform that allows sharing of files or links.
Layered Security with Salesforce Cloud Protection

Safety of External Content for Salesforce Cloud
For more information, please contact:
Sales at 302 715-0062 or This email address is being protected from spambots. You need JavaScript enabled to view it.