New security vulnerabilities are identified every 90 minutes, and several thousands of vulnerabilities are disclosed every year. It takes Clients not using Security Vulnerability Management more than 100 days for a vulnerability to be remediated. Vulnerability management is an opportunity to significantly lower the cost of security. It's less costly to deal with security before serious problems arise than it is to deal with it during a crisis or incident recovery. The C-Suite should be interested in liabilities for data breaches. Executives need to know how strong their company's cyber defenses are, as well as the expected responses for cyber attacks. Vulnerability management allows you to understand how an attacker would target your company and translate that into actionable strategies and risk management.
HANA.EXPERT offers the Healthcare Industry a sophisticated, enterprise-grade vulnerability scanning and management assessments that gives clients control and manage of IT security risks. The goal of a Security Vulnerability Management Assessment is to determine the level of security for an agreed component at any given time. Even though a vulnerability scan can at best give an excellent insight into the level of security for the given target, it should never be used as the sole process for ensuring information security.
An assessment can give an insight, which would otherwise be missed, but it cannot necessarily find all possible weaknesses and vulnerabilities, which would have been visible during the analysis and design phases. That is, a vulnerability assessment can reveal security problems, but it cannot prove the absence of them.
In addition, defense and attack techniques constantly evolve. Sometimes a completely new class of vulnerabilities is discovered, which was simply not known before. For this reason, the results of a vulnerability scan expire as time passes, and it is recommended to regularly assess critical business functions.
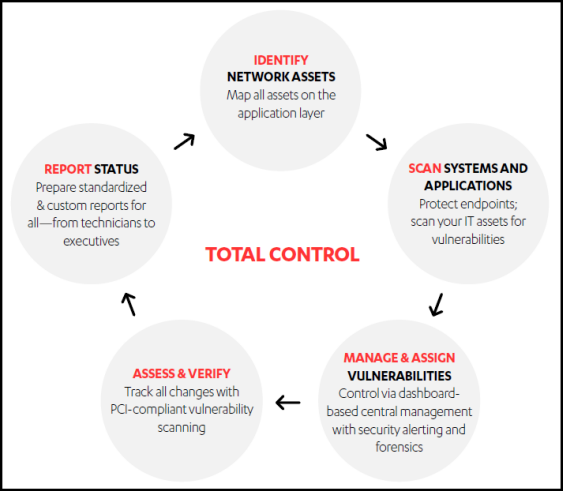
Security Vulnerability Management Assessments allow to identify, categorize and manage vulnerabilities, such as unsecure system configurations or missing security updates in network-attached devices. An assessment allows clients to:
- Discover and identify network-attached IT assets
- Report on the security configuration of IT assets
- Establish a baseline of vulnerability conditions for network-attached devices, applications and databases to identify and track changes in vulnerability states
- Produce reports with content and format to support specific compliance regimes, control frameworks and roles
- Support risk assessment and remediation prioritization with context regarding vulnerability severity, asset criticality and prevalent threat
- Support operations groups with information and recommendations for remediation and mitigation
- Manage and administrate decentralized and distributed scanner instances and architectures.
Vulnerability Management Life Cycle
Scope of a Security Vulnerability Assessment

Total number of Vulnerabilities

Top 10 most vulnerable targets

Top 3 most frequent high/medium risk vulnerabilities

Cyber security is not simple. It is not something that you can say "it is done". Unless you continuously improve your security capabilities, you will not be able to protect your business against emerging threats like ransomware and what comes next.
For more information, please contact:
Sales at 302 715-0062 or This email address is being protected from spambots. You need JavaScript enabled to view it.